| INFORMATION SECURITY SOLUTIONS FOR POWER FACTORIES CONNECTION A0
AN TOÀN THÔNG TIN KẾT NỐI
Information security solutions for power plants connecting to the national dispatching center
– One-way security gateway (abbreviated in English: Undirectional Gateway/Data Diode) is a device designed to be placed between the industrial control network (ICS) area and the business network (Corporate network). This device allows one-way data transmission from the source network to the destination network and does not allow any data from the destination network to return to the source network.
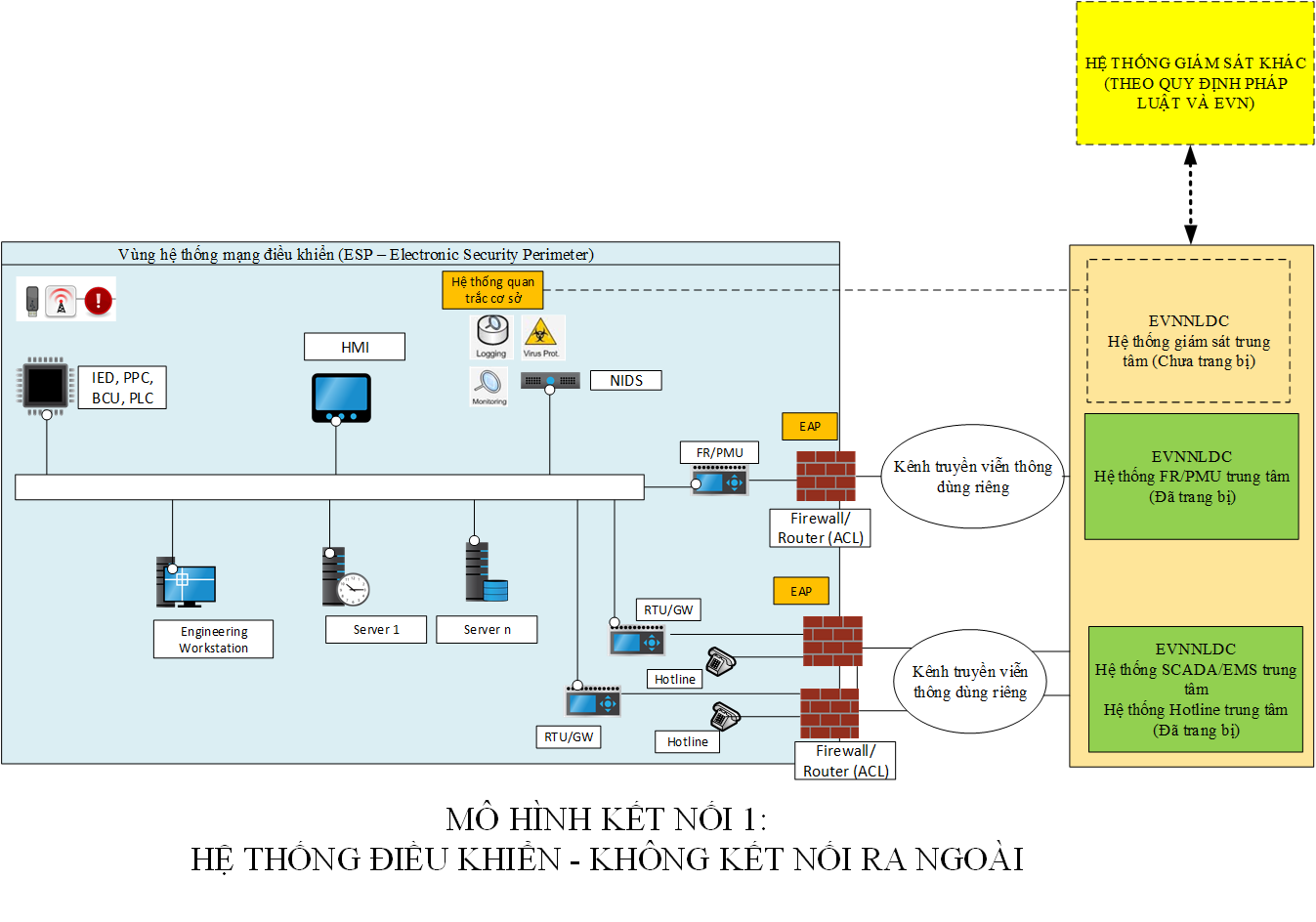
– ESP (abbreviation in English: Electronic Security Perimeter) is the area of the control network system that needs to be protected. This is a network area set up to place servers and workstations used to monitor, collect data and control industrial control information systems that are connected to other networks through routing protocols. .
– EAP (abbreviation in English: Electronic Access Points) are border access control devices. These are network access control devices that have the function of routing and controlling inbound/outbound traffic on the network. For example: Firewall, Router with Access Control List (ACL), Virtual Private Network Server (VPN Server), Unidirectional Gateway, or other security devices.
– Jump Host : An intermediate computer device used to connect remotely to an industrial control information system.
Secure network connection ( abbreviated in English: secure network connection) is the establishment and use of network protocols that support security features (encryption, authentication) to ensure the exchange of information information over a secure network environment. Examples of some protocols: SSH, SSL/TLS, VPN or other equivalent protocols.
System log is the events recorded by the system related to the operating status, incidents, information security events and other information related to the operation of the system (if any). yes).
– NIDS (abbreviation in English: Network Intrusion Detection System) is an anomaly detection system in the network environment. This system monitors network traffic and generates alerts when network attacks are detected based on analysis of these network traffic.
Anti -malware/antivirus software is software that detects, warns and handles malware.
– Basic monitoring equipment is the equipment including hardware and software located at the generating units, the power transmission units. This device has the functions of detecting attacks, risks, and network information security incidents; capable of monitoring all network connections in the ESP area; capable of connecting to the central monitoring system of the electricity system and market operator. An example of a facility monitoring device can be one or more of the following: NIDS, Firewall, IPS, collect/normalize data collected network security information (Connector), Device that stores monitoring data Logging.
– The DMZ (Demilitarized Zone) is a network area set up to place public servers, allowing direct access from external networks and the Internet.
Multi -factor authentication is an authentication method that relies on not only one, but a combination of factors related to the user, including: information that the user knows (password, password, etc.) access codes…), information owned by the user (digital certificates, smart cards…) or information about the user’s biometrics (fingerprints, irises…).
– Remote connection access (abbreviated in English: Interactive Remote Access) is an action by which a supplier, contractor or consulting unit makes a remote connection to an industrial control information system to support support or troubleshooting, or advice.
– Information system includes information technology infrastructure system, information technology system, industrial control system, specialized service information systems.
Tài liệu sản phẩmGiải pháp linh hoạt & đáng tin cậy

Theo yêu cầu KT TTĐQG

Thiết bị chính hãng
dễ sử dụng

Hoạt động trong môi trường
Công nghiệp, tin cậy

Hệ thống có thể mở rộng
YÊU CẦU
– Power plants and substations (NPPs/substations) are required to fully comply with information security regulations promulgated by the Information System Owner/NPP/NPP Operational Management Unit. In addition, Power Plants and Substations comply with solutions to ensure information safety and security




